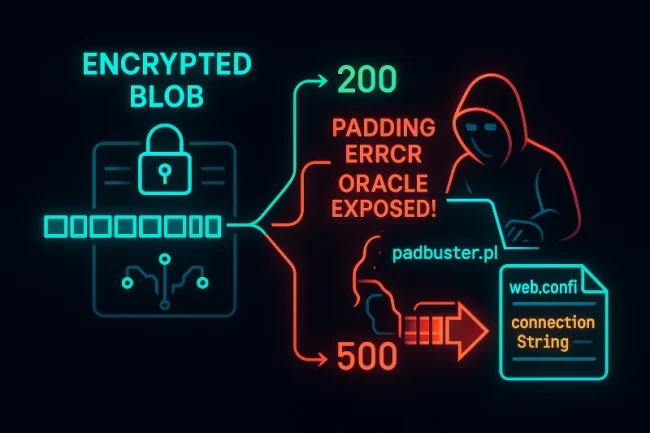
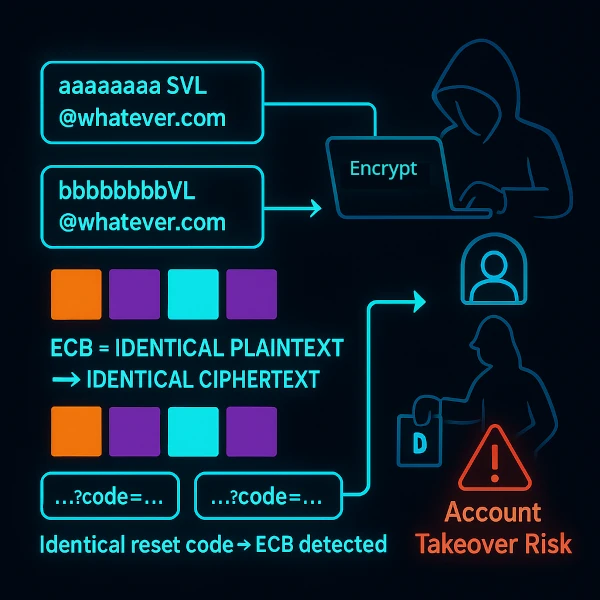
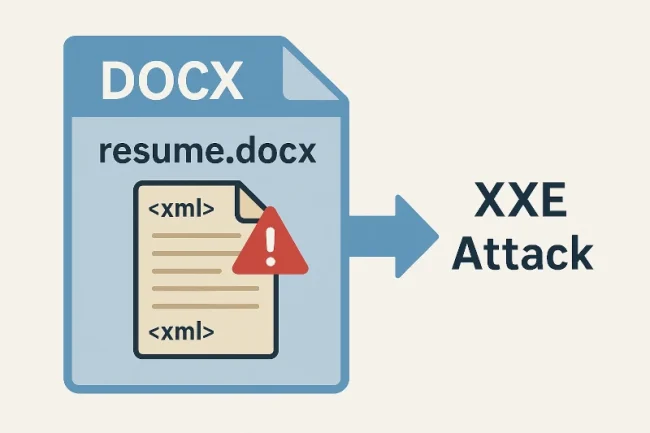
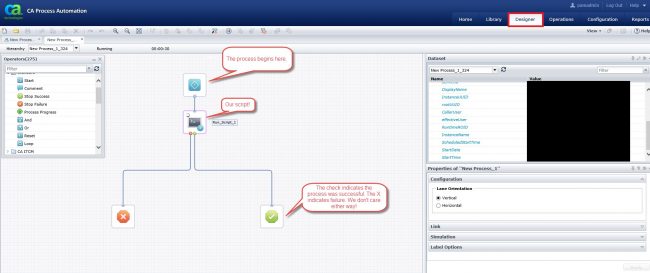
Breaking Crypto – Padding Oracle Attacks
Overview This post presents a lab-based demonstration of a padding oracle attack targeting AES-CBC with PKCS#7 padding. The aim is to illustrate how an oracle that reveals padding errors can be leveraged to decrypt ciphertext—and even encrypt arbitrary plaintext—within a controlled environment, using publicly available tooling.https://en.wikipedia.org/wiki/Block_cipher_mode_of_operation#Cipher_block_chaining_(CBC) A “Padding Oracle” tells you whether or not the…